Netspective Communications LLC acknowledges its obligation to secure data, business systems, and IT resources within its ownership and control. To achieve this, PCII establishes and enforces policies, procedures, and standards that identify key security issues and the responsibilities of individuals, colleges, departments, and units in maintaining appropriate protection for university data and business systems. [FII-SCF-012-IAC-01]
-
The Netspective Communications LLC must ensure that all applications it develops and/or acquires are securely configured and managed. Refer Application Security Policy.
-
The application’s security design must consider and, if possible, apply the following security best practices:
-
Prominently display a confidential record banner if the application processes confidential information, highlighting the type of confidential data being accessed, such as PII or PHI.
-
Do not display sensitive data, especially data restricted by law or policy, in plaintext. [FII-SCF-018-PRI-05.2]
-
Ensure that applications properly and restrictively validate input, allowing only known correct input types, such as cross-site scripting, buffer overflow errors, and injection flaws.
-
Ensure that applications properly execute error handling to avoid providing detailed system information to unprivileged users, denying service, impairing security mechanisms, or crashing the system.
-
Authorize access to applications by affiliation, membership, or employment instead of by individual. If possible, allow users to log on to applications rather than networks. Conduct automated authorization reviews regularly.
-
Encrypt data at rest and in transit. [FII-SCF-008-CRY-05]
-
Implement application logging to the extent practical and retain logs of all users and access events for at least 90 days. [FII-SCF-016-NET-04]
-
Have qualified peers conduct security reviews of code for all new or significantly modified applications, particularly those that affect the collection, use, and/or display of confidential data. Document all actions taken.
-
Implement a change management process for changes to existing software applications.
-
Document the standard configuration of the application.
-
Immediately change default passwords used within the application, such as for administrative control panels or integration with databases upon installation.
-
Do not require the use of special characters or regular rotation for password policies.
-
Do not allow applications to have access to live data during development and testing.
-
-
If acquiring applications from a third party vendor, the organization must:
- Only procure and use applications that are supported by an approved vendor.
- Arrange full support contracts with the application vendor for the full life-cycle support.
- Confirm with the vendor before applying any custom modifications to the application to ensure they can continue to provide support.
- Implement updates, patches, and configuration changes issued by the vendor as soon as possible.
- Conduct a full review of applications and licenses at least annually as part of regular software reviews.
Procedures
Pass utility configured in FCR servers.
-
In Server 1
- Create Private Git Bare Git Repos accessible only through SSH keys + IP restriction.
-
In Server 2
- Generate GPG key with recommended security options, exported and kept the keys safe.
- Initialize a password store.
- Insert and generate passwords using pass utility.
- Initialized the password store as a git repository and pushed to remote bare repository.
-
In Server 3
- Import the GPG keys.
- Git clone the password store from remote bare repository.
- Retrieved the passwords using pass utility.
Password Store Structure
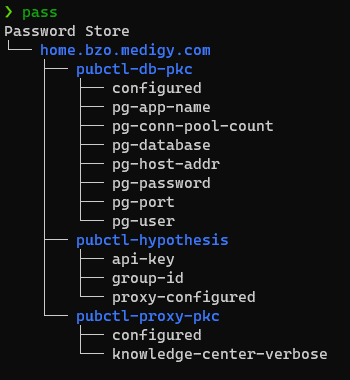
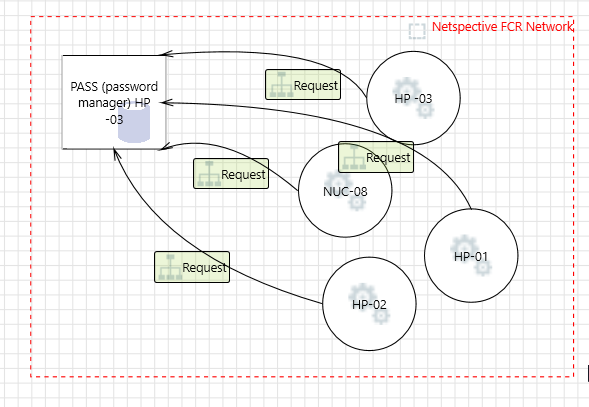
Netspective Communications LLC FCR Network
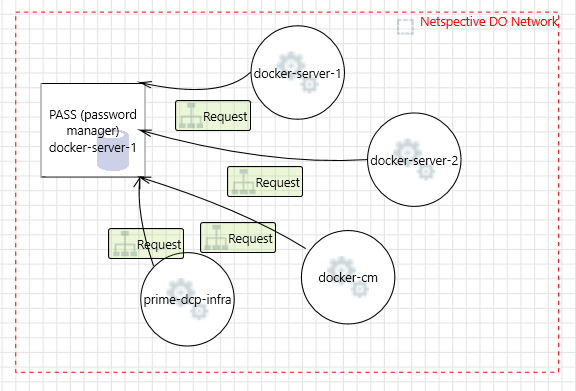
Netspective Communications LLC Digital Ocean Network
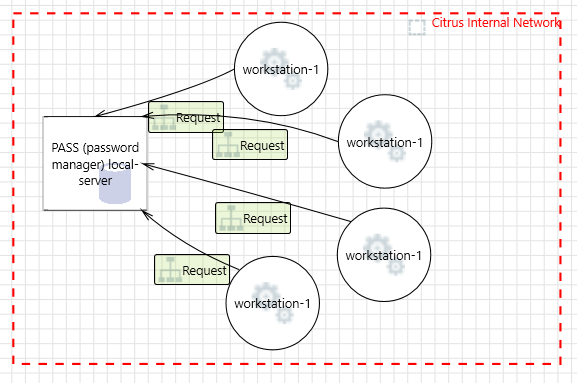
Citrus-Internal Network
Manage pass-based credentials securely across DO, FCR, Citrus, and AWS environments
Setup up GnuPG in Password Store Server:
gpg2 --full-generate-key<br/>
Export the master key-pair and keep it in a safe location.
Initialize an empty password store with master key:
pass init <master-key-signature>
Insert / Generate password entries:
pass insert home.bzo.medigy.com/pubctl-db-pkc/pg-password
Retrieve the password entries:
pass home.bzo.medigy.com/pubctl-db-pkc/pg-password
Managing your password-store with GIT:
Create a private Git in protected
network. Must be Bare Git Repos accessible only through SSH keys + IP
restrictions to SSH port.
In Git server.
git init --bare ~/.password-store
Initialize the password store git repository and push to Git server
pass git init
pass git remote add origin user@git-server:~/.password-store
pass git pushOnboarding creators(devs, BZO, etc.) staff
Setup up GnuPG in creator’s machine
gpg2 --full-generate-key
Export the GPG + SSH public key and share with ops personnel
gpg2 --export --armor <gpg-key-signature> > ~/<firstname>-publickey
Ops person will then import it to the password store server and tell GPG to trust the key and add to the password store like below.
Import the creator’s public key in Password Store Server
gpg2 --import /temporary-path/<firtname>-publickey
Trust the newly added Public key
gpg2 --edit-key <creators-gpg-key-signature>
Type trust and choose the option 5 like below, 5 = I trust ultimately
Add creator’s public key to password store:
vim /root/.password-store/.gpg-id
Append the creator’s signature -
creators-gpg-key-signature as a new line
Re-encrypts the store with current gpg signatures.
pass init $(cat ~/.password-store/.gpg-id)
Push the modifications to git-server:
pass git push
After ops team
added your key to the password store, creators can fetch the store and retrieve
the passwords.
From creator’s machine:
git clone user@git-server:~/.password-store ~/.password-store
Retrieve the password entries:
pass home.bzo.medigy.com/pubctl-db-pkc/pg-password
Off boarding creators(devs, BZO, etc.) staff
Remove creator’s creators-gpg-key-signature from password store:
vim /root/.password-store/.gpg-id
Remove the creator’s signature -
creators-gpg-key-signature line.
Re-encrypts the store with current keys.
pass init $(cat ~/.password-store/.gpg-id)
Push the modifications to git-server:
pass git push
From creator’s machine:
Fetch the latest updates, pass git pull
Retrieving the password entries will show below error:
pass home.bzo.medigy.com/pubctl-db-pkc/pg-password
gpg: decryption failed: No secret key
Then, remove creator’s SSH public
key from remote Git Repository.
Onboarding an operation staff
Import the exported GnuPG master keypair in ops personal machine
gpg --import master-pubkey.asc
gpg --allow-secret-key-import --import master-privkey.asc
Share the SSH public key and fetch the remote password store git
repository
git clone user@git-server:~/.password-store ~/.password-store
Retrieve the password entries
pass home.bzo.medigy.com/pubctl-db-pkc/pg-password
Off boarding an operation staff
Generate new GnuPG master key-pair:
gpg2 --full-generate-key
Replace old master key signature with new one in password store:
vim /root/.password-store/.gpg-id
Remove the old master signature -
master-gpg-key-signature line.
Re-encrypts the store with current active key signatures
pass init $(cat ~/.password-store/.gpg-id)
Delete old Master private/public keys from server
gpg --delete-secret-keys <master-key-signature>
gpg --delete-keys <master-key-signature>
Push the modifications to git-server:
pass git push
From operation staff machine:
Fetch the latest updates,
pass git pull
Retrieving the password entries will show below error:
pass home.bzo.medigy.com/pubctl-db-pkc/pg-password'<br/>gpg: decryption failed:
No secret key`
Then, remove ops person’s SSH public key from remote Git
Repository.
Instant password regeneration upon compromise
Use pass update extension for instantly changing required passwords.
pass update extends the pass utility with an update command which provides an easy flow for updating passwords.
Follow the installation steps from README.
After successfully installed pass update extension, we can follow below commands to update/generate new passwords.
-
Update the password file with new password
pass update -p home.bzo.medigy.com/pubctl-db-pkc/pg-password -
Generate new password and update the password file:
pass update home.bzo.medigy.com/pubctl-db-pkc/pg-password -
Update all the password files in a directory
pass update -p home.bzo.medigy.com/pubctl-hypothesis -
Invalidate someone having an old GPG key
Evaluate current active GPG key signatures in password store,
cat ~/.password-store/.gpg-idCheck who is using each GPG key signatures,
gpg2 --list-keysEdit below file and remove old GPG key signatures,
vim ~/.password-store/.gpg-idRe-encrypts the store with current active keys,
`pass init $(cat ~/.password-store/.gpg-id)’Push the modifications to git-server,
pass git push