The backup and restoration policy is to establish an effective procedure for the backup and restoration policy adopted by Netspective Communications LLC. Netspective Communications LLC considers its data as a valuable asset that could be lost or destroyed due to intentional or unintentional actions. Therefore, it is crucial for Netspective Communications LLC to safeguard its assets by implementing a backup procedure that outlines the necessary actions to protect its data. [FII-SCF-003-BCD-11]
Backup Restoration →
Backup Restoration →
- 2.3 Procedure Invocation
- Procedure must be followed whenever there is:
| Task | Description |
|---|---|
| Request for Backup | Request to Backup information |
| Request for Restoration | Request for restoring stored data from different departments |
-
2.4 Responsibilities
-
Each role involved in this procedure should have main responsibilities as follows:
| Role | Responsibilities |
|---|---|
| Information Security Department | • Evaluate the backup plan
|
| Asset Owner | • Agree and review with the Information Technology Department all the
details of the backup with regard to information assets.
|
| Information Technology Department | • Head of IT will approve the backup plan. • Ensure that the backup and restoration procedure is followed. • Perform all activities required for the backup and restoration procedures (e.g. obtain, prepare the backup media and prepare systems for the backup/ restoration). • Perform the backup procedure. • Perform restoration procedure. • Maintain accurate records of the backup and restoration procedure details and components. |
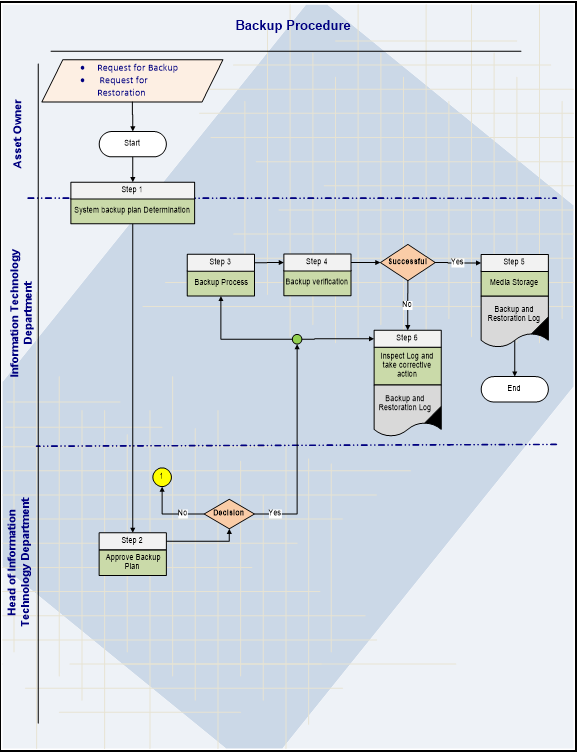
- 3. Procedure Details
- 3.1 Backup Procedures
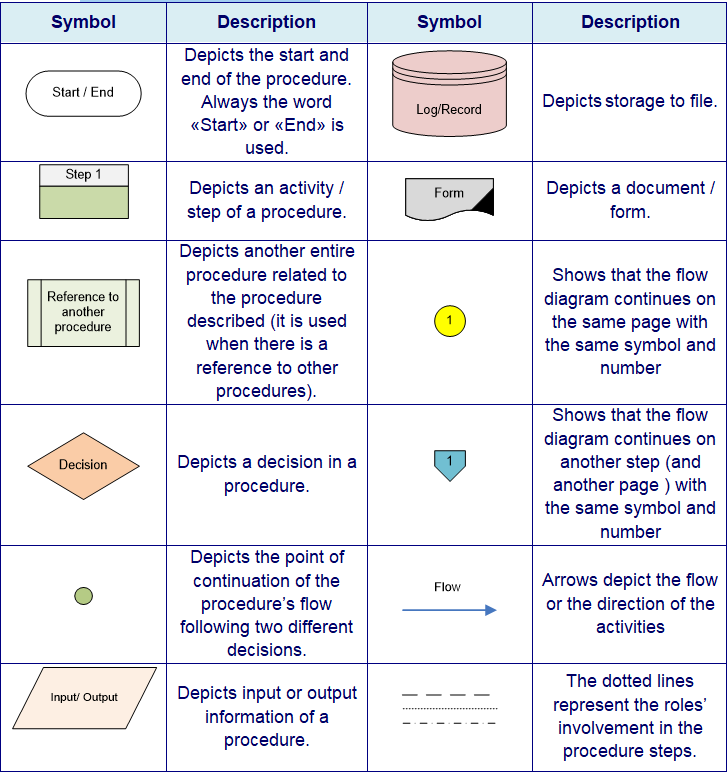
- 3.2 Flow Chart Symbols
- 3.2.1 Backup Procedure Flow Chart Details
-
- Information Technology Department
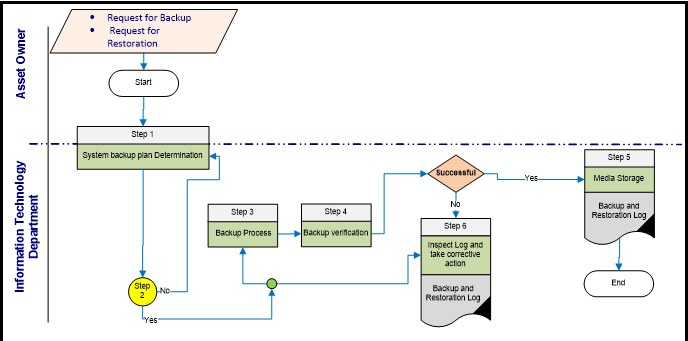
- Information Technology Department
-
- 3.2.1 Backup Procedure Flow Chart Details
- 3.1 Backup Procedures
| Step 1: System Backup Plan Determination | |
|---|---|
| Inputs | Plan requirements. |
| Activities | • With the participation of the asset owner a backup plan needs to be developed, which consists of the following: o Backup scope: what type of information/ data needs the back up (e.g. databases, network settings, file system, etc). o Backup frequency: durations by which back up will be taken (taking into consideration the criticality/ availability factors). o Backup type: is it (full, incremental or online). o Backup mechanism: is it (automatic or manual). o Backup storage location: the storage for the backup media should be in
a secure location on site/off site in different zone if possible. Taking
into consideration the criticality/ availability factors.
o Backup encryption: agree if encryption is required, for which data. o Media labeling: agree on a labeling scheme. o Media destruction: agree on media disposal process.
|
| Outputs | Backup plan. |
| Step 3: Backup Process | |
| Inputs | Approved Backup Plan. |
| Activities | • Perform backup on the systems / network devices.
|
| Outputs | Backup verification. |
| Step 4: Backup Verification | |
| Inputs | Backup Process/ results. |
| Activities | • The backup process will be validated to confirm the success of the process and no problems were encountered by the IT Department (Network / system administrator). • On successful completion proceed to step 5.
|
| Outputs | Decision |
| Step 5: Media Storage | |
| Inputs | Successful Backup Media. |
| Activities | • The IT Department (Network / system administrator) will store the
media as per the backup plan.
|
| Outputs | • Successful Backup Media.
|
| Step 6: Inspect backup Log. | |
| Inputs | Backup log. |
| Activities | • In case of unsuccessful backup process the IT Department (Network /
system administrator) will inspect logs for errors detection and
corrective action will be taken.
|
| Outputs | • Backup Inspection Results. |
-
- Head of Information Technology Department
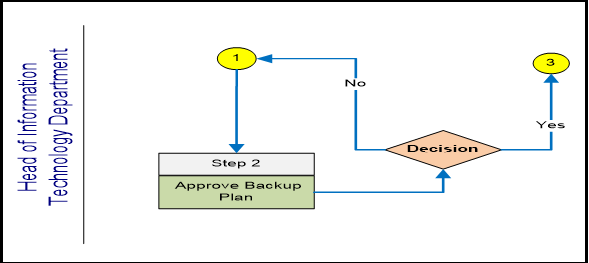
- Head of Information Technology Department
| Step 2: Approve Backup Plan | |
|---|---|
| Inputs | Backup Plan. |
| Activities | • Once the plan has been determined, the Head of Information Technology Department will evaluate the plan and decide on approval. • If plan approved (Yes) Proceed to step3
|
| Outputs | Decision |
- 3.3 Restoration procedure [FII-SCF-003-BCD-13]
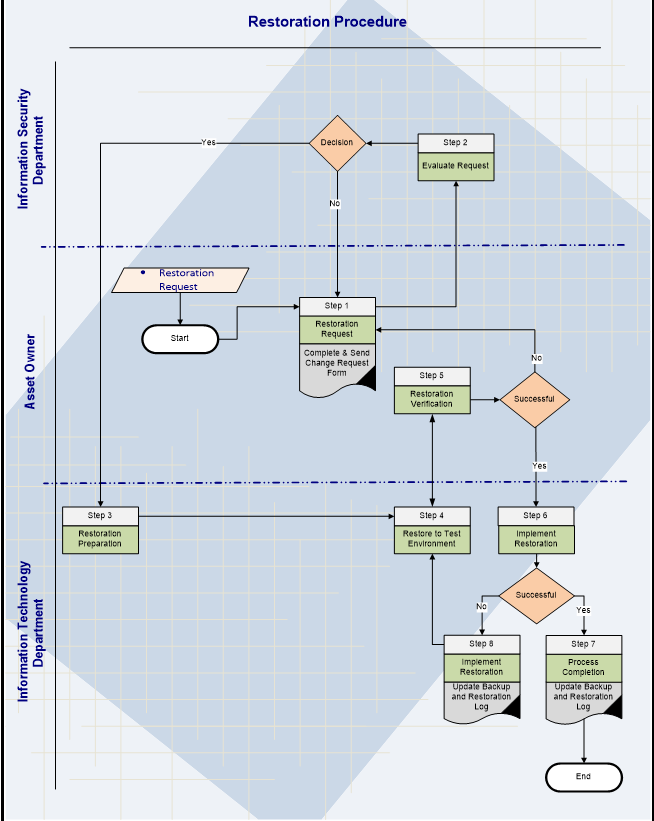
- 3.3.1 Restoration Procedure Flow Chart Details
-
- Asset owner
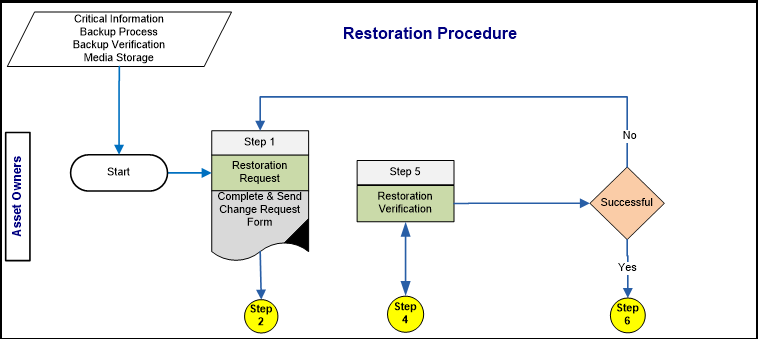
- Asset owner
-
| Step 1: Restoration Request | |
|---|---|
| Inputs: | Business need for restoration. |
| Outputs: | Request form |
| Step 5: Restoration Verification | |
| Inputs: | Test Restoration process completion Results. |
| Activities: | • Asset owner to confirm the success of the Test process, the data is restored completely. And that the data restored is the data needed and requested. • If the process is successful proceed to step 6. • If the process is unsuccessful Go to step 1. |
| Outputs: | Accepted or Rejected Test Results. |
-
- Information Security Department
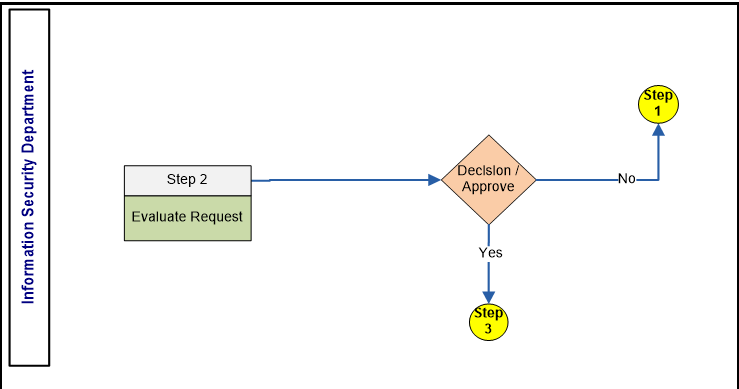
Step 2: Evaluate Request Inputs: Request form. Activities: • The Information Technology Department will evaluate the overall Request.
• If decision approved (Yes) proceed to step 3.
• If the Request is not adequate it will be sent back to the asset owner for update and enhancement, Go to step 1Outputs: Decide for approval -
- Information Technology Department
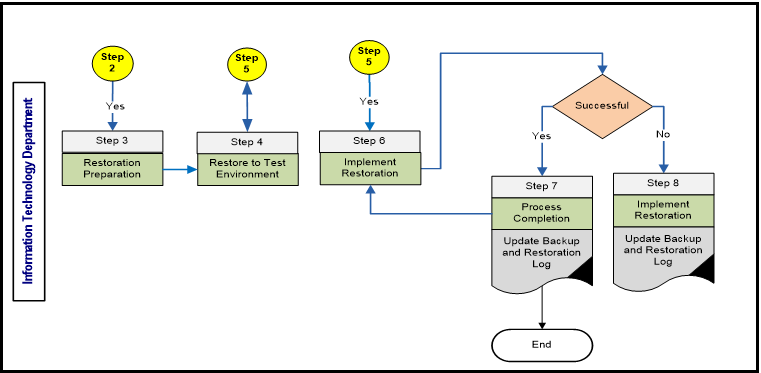
Step 3: Restoration Preparation Inputs: Approved Request Form Activities: • Prepare storage media for restoration.
• Prepare systems / network devices for restoration.
• Proceed to Step 4.Outputs: Prepared system and Storage Media Step 4: Restore to Test Environment Inputs: Prepared system and Storage Media. Activities: • Perform restoration on the systems / network devices on Test Environment.
• Proceed to step 5 for restoration verification.Outputs: Test Restoration process completion Results. Step 6: Implement Restoration Inputs: Reviewed and verified restoration Request will be received from asset owner
Activities: • If restoration is successful proceed to step 7.
• If restoration is unsuccessful proceed to step 8.Outputs: Implementation of restoration. Step 7: Process Completion Inputs: Restoration Process completion on Production system / network devices.
Activities: • Update the Backup and Restoration Log.
• Inform requester.Outputs: Updated backup and restoration Log.
Closed Change Request Form.
Step 8: Inspect Log and correct errors Inputs: Unsuccessful Restoration Process on system / network devices.
Activities: • The logs of unsuccessful restoration process will be inspected for errors, and the errors will be corrected.
• Update Restoration Log.• Update Change Request Form.
• Go to step 4.Outputs: Corrective action.
Restoration Log
Updated Change Request Form.
- Information Technology Department
- Information Security Department